On a previous post I’d recommended using AES-GCM on VPNs to AWS and GCP since it’s generally a more efficient algorithm that offers higher throughput. So it came as a surprised today doing some deep-diving on my Fortigate 60-E today: AES-GCM is supported for Phase 2, it is not supported in hardware on the NPU:
FGT60ETK18XXXXXX # get vpn ipsec tunnel details
gateway
name: 'aws1'
type: route-based
local-gateway: 198.51.100.78:4500 (static)
remote-gateway: 3.140.149.245:4500 (static)
mode: ike-v1
interface: 'wan1' (5)
rx packets: 52 bytes: 6524 errors: 0
tx packets: 110 bytes: 6932 errors: 3
dpd: on-demand/negotiated idle: 20000ms retry: 3 count: 0
nat traversal mode: keep-alive RFC 3947 interval: 10
selectors
name: 'aws1'
auto-negotiate: disable
mode: tunnel
src: 0:0.0.0.0/0.0.0.0:0
dst: 0:0.0.0.0/0.0.0.0:0
SA
lifetime/rekey: 3600/3289
mtu: 1438
tx-esp-seq: 2
replay: enabled
qat: 0
inbound
spi: 7dbc0283
enc: aes-gc 35a72036fa9a87000c90415b1863827652bf9dfd875f28a6d20fd1569e5c0099de639dcc
auth: null
outbound
spi: ccdb6ab8
enc: aes-gc 21dd5c71a83142b0ecee1efe2c000c0dae586054160eb76df6f338d9071380b12103b0d9
auth: null
NPU acceleration: none
FGT60ETK18XXXXXX # get vpn ipsec stats crypto
NPU Host Offloading:
Encryption (encrypted/decrypted)
null : 0 0
des : 0 0
3des : 0 0
aes-cbc : 833309 0
aes-gcm : 0 0
aria : 0 0
seed : 0 0
chacha20poly1305: 0 0
Integrity (generated/validated)
null : 0 0
md5 : 0 0
sha1 : 803671 0
sha256 : 29540 0
sha384 : 48 0
sha512 : 50 0
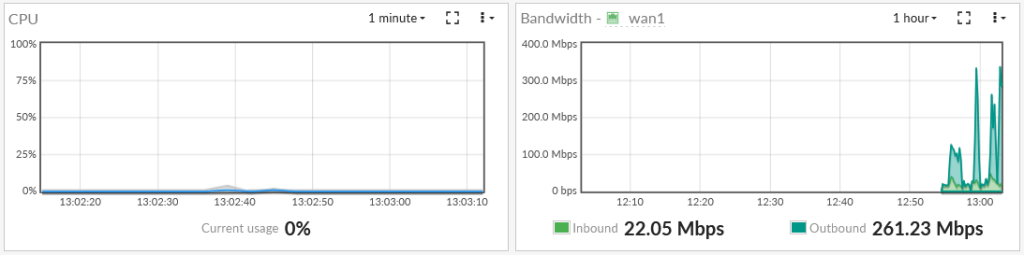
Since the hardware offload isn’t occurring, the main CPU is moderately taxed when doing transfers via AES-GCM. Also, the throughput is only ~ 100 Mbps:

Reconfiguring the VPNs to AES-CBC and redoing the transfers, we get lower CPU usage and significantly higher throughput: